Anonymization is the disguising of the start and destination point of a connection that exists for communication or data exchange. A fundamental characteristic of anonymization is the removal of characteristics that allow conclusions to be drawn about the user.
Anonymisation is required because it may not be sufficient to encrypt communication in order to effectively protect oneself on the Internet. The connection data, for example IP addresses, remain open. Even if attackers and supervisors cannot see the contents of the communication directly, they can still see what kind of communication it is and with whom the communication exists or from where the information was retrieved. For effective data and communication protection, it may therefore be necessary to disguise the start and end points of the communication. Anonymisation services or networks are used for this purpose.
IP address as identification feature
The IP address plays a central role in the identification of Internet users. In Internet communication, data exchange takes place on the basis of data packets that are exchanged between clients and servers. For this purpose, the data packets are provided with the IP addresses of sender and receiver so that the received data packets can be assigned to the respective communication partner on both sides. When data packets are transmitted, the IP addresses are also required for routing to the destination. This means that the IP address can be viewed by anyone who receives the data packet. Since the route taken by a data packet on the Internet is more or less random, you can never be sure that the data will not be picked up and analyzed somewhere. Even if the data itself is encrypted, some information about the communication partners can be determined via the IP addresses.

For example, a Whois query leads to the Internet provider used. Since Internet providers use IP addresses locally, it may be possible in combination with a geolocation service to find out the city, perhaps even the district. Advertising networks already use these services to place regional advertisements. In online shopping, creditworthiness is calculated on the basis of location information.
Although IP addresses are often assigned dynamically, they may change with each session. However, there are other ways of securely identifying an Internet user.
IP address obfuscation options
Because the IP address plays a central role in the identification of Internet users, anonymization techniques are used to conceal them. The correct IP address is replaced by another IP address. On the way to the Internet, one or more address changes or address translations are carried out somewhere. The data packets are forwarded via a forwarding server (proxy), a VPN gateway or an anonymization network. This is where anonymisation takes place.
Proxy
The use of a proxy is the easiest way to move anonymously on the Internet. All you have to do is enter the IP address of the proxy in the network settings of the client or in the browser.
 Proxy means deputy. It accepts requests from clients and forwards them to the target server on the Internet. The server only sees the IP address of the proxy and not of the client. In the opposite way, the proxy receives the data packets from the server, exchanges the IP address and forwards them to the client.
Proxy means deputy. It accepts requests from clients and forwards them to the target server on the Internet. The server only sees the IP address of the proxy and not of the client. In the opposite way, the proxy receives the data packets from the server, exchanges the IP address and forwards them to the client.
With this constellation one must consider that the returned data can be stored and evaluated by the proxy. A proxy is a “man in the middle” that is anonymous, but whose operator must be trusted unconditionally. A supposedly anonymizing proxy can also spy out passwords and rewrite requested web pages without the user noticing anything on the client side.
VPN gateway / VPN tunnel
VPN services are another possibility for anonymization. VPN software is installed on the client, which forwards all data traffic to a VPN gateway on the Internet. The gateway exchanges the IP addresses so that the target servers on the Internet only see the IP address of the VPN gateway. The data traffic between client and gateway is encrypted. However, data traffic is normally transferred between the gateway and the server. Read more at plural.mx.
In principle, the VPN gateway does nothing other than a proxy. Only that the functions of the VPN gateway are mostly based on hardware and therefore work faster than proxies. Proxies are typically installed as a service on a server. The speed then depends not only on the network connection, but also on the load.
Typically, it is not the task of a VPN gateway to record data traffic. However, this does not mean that the operator does not do it after all. For example also connection data. It would also be conceivable that secret services, criminal investigators or other attackers could latch into the VPN gateway and monitor communication or access data traffic. The user must encrypt the data via the VPN gateway before it is sent so that the data cannot be seen by others. Provided that the recipient can decrypt the data.
In addition, you should use a public DNS server instead of the standard DNS server of your own provider, because website operators can find out the actual IP address of the visitor via a forced DNS query, which is based on an embedded image on a subdomain.
Tor – The Onion Router
 Anyone who seriously wants to anonymise has to put in more effort. It is not enough to conduct data traffic via a proxy or a VPN gateway. One option would be onion routing, as used in the Tor anonymization network.
Anyone who seriously wants to anonymise has to put in more effort. It is not enough to conduct data traffic via a proxy or a VPN gateway. One option would be onion routing, as used in the Tor anonymization network.
Tor obscures the IP address of an Internet user by using multiple nested encryptions across multiple stations. For the target server, it looks like access is coming from a Tor network computer connected between the user and the server. Because of the nested encryption, Internet connections over the Tor network are much slower. Watching videos, VoIP telephony and online gaming are hardly possible.
Mix cascades are another principle of anonymization. These are chains of servers that encrypt data packets so that only the server at the end of the chain can decrypt them. The mixes, as the servers are called, first collect the data packets in order to forward them in random order. Pseudo data packets between the mixes are intended to make monitoring even more difficult.
Mix cascades at JonDonym (commercial service) are fixed and do not change during the connection. The user may choose the mixes himself and can consist of 2 or 3 servers, one of which should be located abroad. In this way it is difficult for investigating authorities to penetrate the complete mix cascade. Cross-border cooperation between investigating authorities and secret services would be necessary in order to obtain the connection data.
JonDonym does not offer absolute anonymity either. As soon as the attacker has access to all mix cascades taken by the data traffic of a certain user, anonymity is broken. However, mix cascades with JonDonym are much more secure than proxies or VPN gateways. The mix operators are all known and equipped with certificates. Also with JonDonym it cannot be excluded that attackers and supervisors gain access to the Mix servers. However, the risk is lower than with the Tor network.
What anonymization cannot do
- Effective anonymisation depends on the integrity of the operator and the trust of the user. In principle, the operator of the anonymization service or network may not record or evaluate any data. In principle, no connection data. Especially not over the period of time during which the connection lasts.
- While data retention is suspended in Germany, telecommunications providers, including anonymization services, in other European countries have to store their customers’ connection data for several months. For this reason, anonymization is only possible to a limited extent. Anyone who commits an online offence should be aware that they can be deanonymized despite anonymization.
- In order to protect oneself effectively against anonymisation by secret services, it is advisable to refrain from using the services of providers with headquarters or parent companies in the USA, Canada, Great Britain, Australia, New Zealand and Sweden. The secret services of these countries access data traffic on the Internet or have access to personal data of large Internet services.
Anonymization can become a security risk
Making data traffic anonymous is an extremely atypical process. In comparison, the encryption of data is common for many Internet users, even unknowingly. For example, in online banking or online shopping.
On the other hand, anyone who additionally anonymizes data must be aware that they are acting conspicuously. Attackers and supervisors assume that anonymous communication has something to hide. This can be the reason for an attacker or supervisor to record the communication and take measures to deanonymize it. The use of anonymization techniques or services to gain more security for data or communication can therefore have exactly the opposite effect. It reduces the security of communication and data transmission.

Identification via Cookies / Deanonymization via Cookies
For the sake of completeness, it should be noted that IP addresses are not the only identifier. If you are using a browser, the IP address is not the only identifier, but cookies, which are used to recognize returning visitors. Cookies are data records that are stored on the user’s computer. Usually as a text file. Personalized services are dependent on the data contained therein.
- Web pages that display advertisements go one step further and place third-party cookies on the computers of their visitors. In this way, the advertising provider can track the user across web pages. Third party cookies must generally be blocked. They are used exclusively for tracking the websites visited. Not to use them means no loss of comfort.
- In addition to cookies, there are other ways to identify users. Active content, such as Flash, Java and Javascript, can cancel out anonymisation measures. For example, if proxy solutions or anonymization networks such as JonDonym or Tor are used.
- Activated Javascript can reveal the real IP address, even if it has been obfuscated using Tor or JonDonym. Effective anonymization requires the deactivation of active content. Unfortunately, it is often the case that websites without Javascript are not or only with difficulty accessible.
Browser Anonymization
In particular, the advertising industry is constantly coming up with new techniques to recognize a user. A typical example is the setting of cookies on the website visitor’s computer. But even if the user has switched off cookies, there is still DOM storage and, in case of doubt, fingerprinting (browser version, resolution, window size, plugins, …), which can be used to recognize the user.
For this there is the concept of an anonymizing browser. For this purpose, the web content is not rendered in the user’s browser, but in the browser within a sandbox on an anonymization server. From there, the web content is then transferred to the user’s browser. All elements and content that could identify or even endanger the user are concealed and executed on the server. This includes obfuscating the IP address, setting cookies and executing Javascript on the server.
However, the server serves as a proxy, which means that the data is passed on to third parties. This is a problem if, for example, you do online banking or otherwise have to authenticate yourself.


 Use the email and groupware features of an Exchange server without your own hardware. For example, we set up a Microsoft Exchange Server in our data center, which offers you the same functions as the variant with its own server.
Use the email and groupware features of an Exchange server without your own hardware. For example, we set up a Microsoft Exchange Server in our data center, which offers you the same functions as the variant with its own server.
 I understand what you are thinking–but look: There are so many reasons why people performe a web-based personal history check about others, and they aren’t all always questionable.
I understand what you are thinking–but look: There are so many reasons why people performe a web-based personal history check about others, and they aren’t all always questionable.
 But whosoever the creator is, he has to be acknowledged for a completely thought-out program, which over time has got the capacity. As a symbol of esteem, the lowest divisible number of bitcoin, which will be one-hundred millionth of a bitcoin, continues to be called “Satoshi” subsequent to the creator. To keep an eye on bitcoin follow Coinbase. Here you find a good
But whosoever the creator is, he has to be acknowledged for a completely thought-out program, which over time has got the capacity. As a symbol of esteem, the lowest divisible number of bitcoin, which will be one-hundred millionth of a bitcoin, continues to be called “Satoshi” subsequent to the creator. To keep an eye on bitcoin follow Coinbase. Here you find a good 

 Q: May my pre-paid phone be revealed on request?
Q: May my pre-paid phone be revealed on request? Q: May my cellular telephone service provider will not un Lock my cellphone because they are owed money by me or am presently under contract?
Q: May my cellular telephone service provider will not un Lock my cellphone because they are owed money by me or am presently under contract?
 With all the costs mentioned above, you get:
With all the costs mentioned above, you get: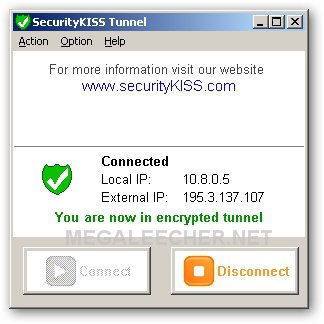
 For iPhone VPN information visit
For iPhone VPN information visit